$ ~/Downloads/lcov-1.10/bin/lcov --capture --directory . --output-file coverage.info
Capturing coverage data from .
Found gcov version: 4.2.1
Scanning . for .gcda files ...
Found 49 data files in .
Processing .libs/buffer.gcda
Processing .libs/bufferevent.gcda
Processing .libs/bufferevent_filter.gcda
Processing .libs/bufferevent_pair.gcda
Processing .libs/bufferevent_ratelim.gcda
Processing .libs/bufferevent_sock.gcda
Processing .libs/evdns.gcda
Processing .libs/event.gcda
Processing .libs/event_tagging.gcda
Processing .libs/evmap.gcda
Processing .libs/evrpc.gcda
Processing .libs/evthread.gcda
Processing .libs/evthread_pthread.gcda
Processing .libs/evutil.gcda
Processing .libs/evutil_rand.gcda
Processing .libs/evutil_time.gcda
Processing .libs/http.gcda
Processing .libs/kqueue.gcda
Processing .libs/libevent_openssl_la-bufferevent_openssl.gcda
Processing .libs/listener.gcda
Processing .libs/log.gcda
Processing .libs/poll.gcda
Processing .libs/select.gcda
Processing .libs/signal.gcda
Processing test/test-changelist.gcda
Processing test/test-dumpevents.gcda
Processing test/test-eof.gcda
Processing test/test-fdleak.gcda
Processing test/test-init.gcda
Processing test/test-time.gcda
Processing test/test-weof.gcda
Processing test/test_regress-regress.gcda
Processing test/test_regress-regress.gen.gcda
Processing test/test_regress-regress_buffer.gcda
Processing test/test_regress-regress_bufferevent.gcda
Processing test/test_regress-regress_dns.gcda
Processing test/test_regress-regress_et.gcda
Processing test/test_regress-regress_finalize.gcda
Processing test/test_regress-regress_http.gcda
Processing test/test_regress-regress_listener.gcda
Processing test/test_regress-regress_main.gcda
Processing test/test_regress-regress_minheap.gcda
Processing test/test_regress-regress_rpc.gcda
Processing test/test_regress-regress_ssl.gcda
Processing test/test_regress-regress_testutils.gcda
Processing test/test_regress-regress_thread.gcda
Processing test/test_regress-regress_util.gcda
Processing test/test_regress-regress_zlib.gcda
Processing test/test_regress-tinytest.gcda
Finished .info-file creation
$ ~/Downloads/lcov-1.10/bin/genhtml coverage.info --output-directory html
Reading data file coverage.info
Found 54 entries.
Found common filename prefix "LibeventLibrary"
Writing .css and .png files.
Generating output.
Processing file source/bufferevent.c
Processing file source/kqueue.c
Processing file source/evmap.c
Processing file source/http.c
Processing file source/evthread-internal.h
Processing file source/evthread_pthread.c
Processing file source/select.c
Processing file source/bufferevent_openssl.c
Processing file source/buffer.c
Processing file source/bufferevent_ratelim.c
Processing file source/bufferevent_pair.c
Processing file source/poll.c
Processing file source/evutil.c
Processing file source/evutil_rand.c
Processing file source/evthread.c
Processing file source/evutil_time.c
Processing file source/evdns.c
Processing file source/signal.c
Processing file source/evrpc.c
Processing file source/log.c
Processing file source/bufferevent_sock.c
Processing file source/event_tagging.c
Processing file source/listener.c
Processing file source/minheap-internal.h
Processing file source/event.c
Processing file source/bufferevent_filter.c
Processing file source/test/regress_ssl.c
Processing file source/test/regress_listener.c
Processing file source/test/regress_thread.c
Processing file source/test/test-eof.c
Processing file source/test/regress.gen.c
Processing file source/test/test-init.c
Processing file source/test/regress_bufferevent.c
Processing file source/test/test-fdleak.c
Processing file source/test/regress_dns.c
Processing file source/test/test-time.c
Processing file source/test/regress_util.c
Processing file source/test/regress.c
Processing file source/test/tinytest.c
Processing file source/test/regress_main.c
Processing file source/test/test-weof.c
Processing file source/test/regress_http.c
Processing file source/test/regress_et.c
Processing file source/test/regress_minheap.c
Processing file source/test/regress_finalize.c
Processing file source/test/regress_rpc.c
Processing file source/test/test-dumpevents.c
Processing file source/test/regress_buffer.c
Processing file source/test/regress_zlib.c
Processing file source/test/test-changelist.c
Processing file source/test/regress_testutils.c
Processing file /usr/include/libkern/i386/_OSByteOrder.h
Processing file /usr/include/secure/_string.h
Processing file /usr/include/sys/_structs.h
Writing directory view page.
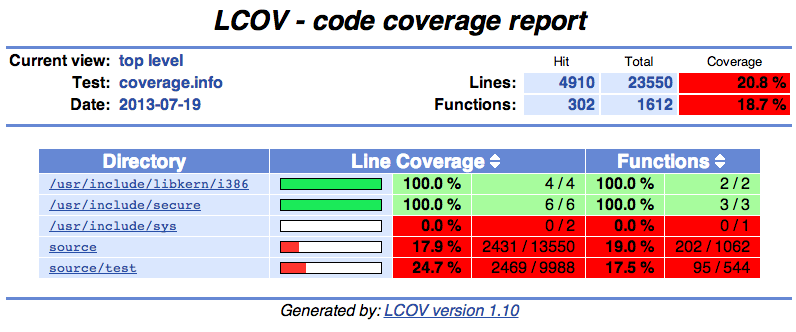
Overall coverage rate:
lines......: 14.5% (3415 of 23550 lines)
functions..: 12.5% (202 of 1612 functions)