VirtualBox has a pretty good remote desktop server built in, but securing it can be a pain if you’re actually doing it properly, using Transport Layer Security (TLS) certificates and the like.
I’ve created a script to handle setting these certificates and username/password pairs, based on the VirtualBox manual, but it seems almost overkill to me for my use case.
There’s an easier way to do it if you’re not trying to set up a whole bunch of headless VirtualBox instances for many different people. The trick is to set the authentication type to Null, but only start the Remote Desktop server on localhost:
If you’re using the secure-box-rdp.sh script I wrote, this is simplified to:
./secure-vbox-rdp.sh -v virtual-machine-name -N -P remote-desktop-port
You just provide the virtual machine name and port number you’d like to use, and the script does the rest.
Then, all you have to do is set up an SSH tunnel into the virtual machine host, and none of the VMs set up this way are exposed to the outside world. Better still, it’s not clear how hard of a security audit the VirtualBox TLS implementation has gone through, but SSH is the constantly-reviewed bedrock of internet security.
Using plink on windows, it looks something like:
plink -v -ssh -l yourloginname -L 5000:localhost:5000 -C -N some.domain.com
Using ssh, it looks something like:
ssh -fCNq -L 5000:localhost:5000 yourloginname@some.domain.com
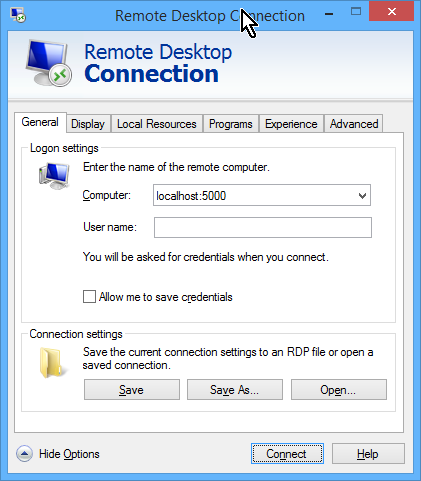
Once the tunnel is connected properly, you can just connect to the virtual machines via localhost:VRDE_PORT, and all of the tunneled traffic is automatically encrypted, for the win!