So I may or may not have bought a new laptop recently, and it may or may not have been a Lenovo.
tl;dr: It was a Lenovo, and there are some things you might want to uninstall from your Lenovo.
I’m kind of in awe of how sneaky these guys are, in terms of the stuff they preinstalled on the system. Some of it appears to be straight-up spyware (otherwise known as “user-experience enhancement” software) of some sort, and I’m trying to figure out what these programs do before I wipe them off the system.
Note: I made sure not to use any of my internet passwords or internet services before I had a chance to take a closer look at the three programs in particular, which I do not trust. I’m also writing this blog post from the new laptop only after uninstalling the programs.
The three programs are:
- CCSDK
- GDCAgentSetupRed
- UESDK
All three programs come preinstalled, and survived the upgrade from Windows 8.1 with Bing to Windows 10. All three programs are written by Lenovo. None of the programs are described openly by Lenovo. So that’s minus points for transparency already.
CCSDK
The CCSDK has a log file folder, CCSDK\log, which seems to gain a log file every time you restart the computer.
Let’s look at the contents of 20150824-013917.2528. Oh, that’s nice, it’s reporting something to someone, somewhere:
I wonder what WinGather.exe is, what it gathers, and what it sends.
GDCAgentSetupRed
The GDCAgentSetupRed app has a log file folder, GDCAgentSetupRed\log, which seems to gain a log file every time you restart the computer.
20150823-181345.4688 looks like this, and the other files look similar:
Question: What is it telling the Lenovo server, and why?
I’m not sure what the answer to this is, as I didn’t get a chance to run Wireshark against the programs, before uninstalling them. Also, I noticed that Ccleaner removed some files related to Lenovo from the Windows Temp folder, but I forgot to check there after uninstalling the Lenovo apps.
Additionally, two files are regularly updated in the GDCAgentSetupRed folder, database.db and sendlog.txt:
Let’s take a look at sendlog.txt. Oh look, it’s filled with timestamps. That’s nice. I’m glad to know our Chinese overlords are aware of when I’m using my laptop:
Let’s take a look at database.db, maybe it’s in a standard format we can decipher? I tried using SQLite Database Browser, but it doesn’t recognize the file format. If someone has a better idea on how to crack this file, get in touch with me, and I’ll send it to you. Who knows, maybe you’ll get my admin password (which would suck), but then if it’s in there, we all have much bigger problems.
UESDK
UESDK\uehelper.log
UESDK doesn’t have a log file folder, but it does have uehelper.log, which looks like this:
The 80M4002DUS identifies what model of laptop I bought, which the astute reader could google easily enough. (Admittedly, it’s not a bad little laptop for the money, either.)
The row with dashes actually seems to be some kind of unique identifier, and there were a lot more digits in there, which I’ve blanked out for obvious reasons. I’m not sure how the identifier is formed, I checked the network MAC addresses, but it doesn’t seem to be using those.
The 2015-06-05 11:06:44:411 timestamp was the time of manufacture / initial power-on date for the machine. This matches up nicely with the identifiers on the shipping box that indicated a ship date of 2015-06-08.
The 2015-08-24 07:48:11:361 timestamp matches up with the start of the current Windows login session.
Network Sockets
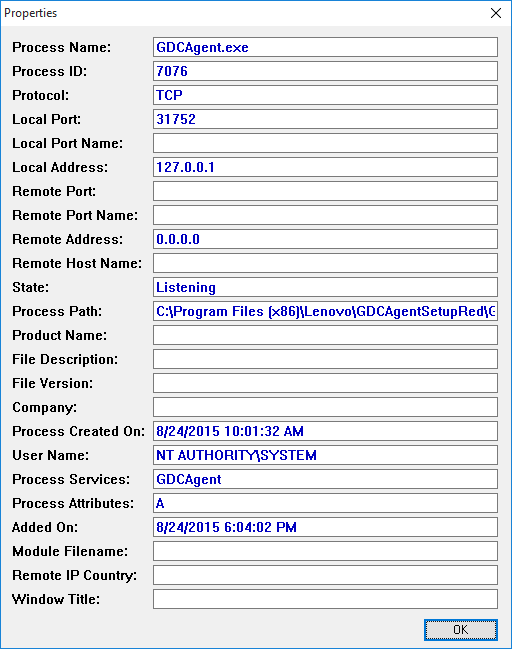
The GDCAgent.exe program will listen to connections on localhost port 31752. I’m not sure what exactly it does with this open port, though:
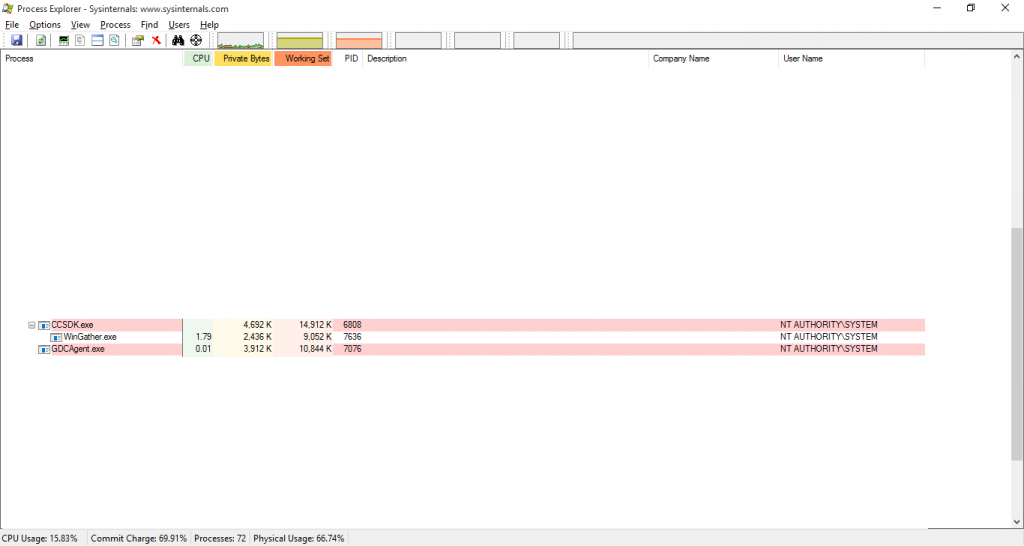
Process Explorer
Digging into the process tree on the system reveals that Lenovo’s three programs run with pretty high credentials.
Programs like these can do just about anything they want to a system: restart it, shut it down, rewrite firmware, and so on. Also irritating, neither the Description column nor the Company Name column are filled in.
So what, exactly, do these programs do?
Final Thoughts
For $180 including tax, the laptop was a pretty good deal, it’s only $80 more than getting a Windows license. But it’s buyer beware, with these dubious pieces of software running at all times on the system.
After uninstalling all of the Lenovo preinstalled software, I noticed no difference in the functionality of the laptop. The volume up / volumn down function keys, the brightness up / brightness down keys worked fine. So by that logic, the extra apps that they installed perform no role but to report back to Lenovo every time you turn the computer on or off.
This is not why we buy computers.
Thank you for writing this article and for including the log snippets. I did some digging and found this same exact software running on my new machine. A big AMEN to your closing comment “This is not why we buy computers.”
On a related note, one of the items you listed is a component of SuperFish. If you do some searches on SuperFish + Lenovo you will discover that you have a suspect certificate installed for both IE and Firefox that permits a “man in the middle” attack when visiting websites that ought to be secure.
Thanks for the heads up on SuperFish. More things to dig into when I next use that machine.
Good job documenting this. Pity there isn’t a more obvious way to remove this junkware. Maybe I should have done a clean install!
Thanks for the article. I’ve been wondering about what this software does, too.
Lenovo laptop I looked at had SHAREit installed, a file sharing application enabled at startup.
I deleted it, reboot and it is back.
The startup had an “if not exists” script pointing to SHAREit/shellext/shellext64.bak and it was reinstalling it from a backup, lol.
The GDCAgentSetupRed directory has an interesting text file called “China” which contains thousands of Chinese network and broadcast addresses. Could this be where the logs are going?
Certainly a possibility. Pretty sure I also moved its Windows Firewall rules to deny all outbound. It’s sneaky software indeed.